Updated: 06/02/2023
This KB article explains the remote connection options to the Liquid Web terminal servers that are available to customers for accessing RDPWin. The document also discusses credit card implications. Customers connect to the hosted servers via Remote Desktop Services. Customers must decide whether or not they need to use the Cisco VPN client or have their public facing static IP address whitelisted in the hosted firewall. The customer may make use of both options depending on the physical location of their employees. These same options are available to support and sales.
Option 1: Remote Desktop Services whitelist method
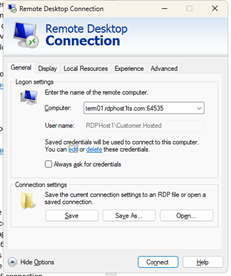
This is the preferred method for hosted customers to connect to RDPWin. This method is secured by whitelisting the customer’s public facing static IP address in the hosted firewall for port 64535, (the hosted terminal servers listen on port 64535 for RDP connections instead of the default port of 3389). Therefore, if a user’s static IP address is not whitelisted in the firewall, they will be blocked from using RDS to access any server in the LW hosted environment. This also secures the port from DoS attacks and other malicious traffic. RDS connection from the client to the hosted server is secured by an SSL certificate, (*.rdphost1ts.com issued by GoDaddy) that is installed in the hosted firewall.
Advantages:
-
Easy to setup and use
Disadvantages:
-
The customer must have a static IP address
-
Employees outside the office will not be able to connect without first using the VPN method or a VPN connection into their office. See LW Support Connection link above.
-
Shift4 customers will still need a VPN connection for their EMV devices and local UTG.
-
Customers with premise-based POS, PBX, etc. interfaces will still need a VPN connection for the interface computers.
Option 2: VPN method
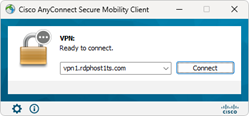
This is the next preferred method for hosted customers to connect to RDPWin. Before using Remote Desktop Services, the customer must connect/authenticate with the Liquid Web firewall using the Cisco AnyConnect VPN Client. The client is downloaded from the LW firewall during initial configuration. See Hosted VPN configuration in the link above. Once the user connects with the VPN client, they are able to use RDS to connect to a LW terminal server via a local IP address that is assigned to their machine via VPN client. The VPN client creates a secure connection via the local machine and the hosted terminal server. This is the preferred industry standard for using Remote Desktop Services.
Advantages:
-
No need for a static IP address
-
Users can securely connect to the hosted environment from any internet connection.
-
Required for Shift4 EMV devices
Disadvantages:
-
Difficult to configure. Most customers require assistance from RDP or their IT staff.
-
Customers must login twice
-
VPN must continually run
Option 3: RDWeb method
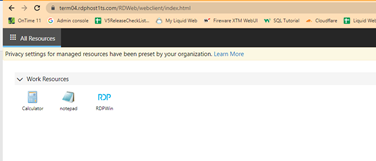
RDWeb, (more info here) uses HTML to allow users to access applications on a terminal server via their browser. You can test this method by going to https://term04.rdphost1ts.com/RDWeb/webclient/index.html in a browser and login with your normal LW Hosted credentials. Under work resources are the published applications that you can access. The main advantage of this option is that RDPWin appears to run in a browser. The main disadvantage is that there is no option to print to a local printer. RDWeb does not redirect the user’s local printers. Instead, RDWeb uses a virtual printer to transfer print jobs as a pdf to the hosted user’s machine. The user can then open the pdf and print it.
Hosted Credit Card Security Concerns over RDS:
Remember that RDPWin does not save a credit card number. Only CC tokens are saved in RDPWin. All credit card communication is encrypted at device and then sent over a secure connection. EMV devices do not use the RDS connection. SRED key devices do use the RDS connection.
RDPPay:
-
EMV devices do not use RDS or a VPN connection to connect to the hosted environment. The device is called by RDPPay, which receives the credit card information from the EMV device and then sends RDPWin a token.
-
The SRED Key device sends the encrypted string over a secured RDS connection to the hosted server. The string is stored in a temporary variable outside of RDPWin, the encrypted string is then passed to RDPPay. A token is then returned by RDPPay and saved in RDPWin.
Tenerum:
-
EMV Devices do not use the RDS or VPN connection to connect to the hosted environment. The device is called by Tenerum which receives the credit card information from the EMV devices and then sends RDPWin a token.
-
The SRED Key device sends the encrypted string over the RDS connection. The string is entered in a HTML form which is then sent to Tenerum. Tenerum returns a token to RDPWin.
Shift4
A VPN connection to the hosted environment is required in order to use an EMV device with Shift4. Go here for information on Shift4, Hosted, and UTG configuration - https://docs.google.com/document/d/0B-R0_hUtBY9xSFFUTFJSYnhDNG8/edit?usp=share_link&ouid=110528267290438072920&resourcekey=0-FiAQH-FcAV9qvfdnilo-OA&rtpof=true&sd=true
Here is a PDF on Shift4 EMV communication: https://drive.google.com/file/d/1LWKIwEUpYzAp5q6-yywebwNQhg1_5JHE/view?usp=sharing
SRED Key works similar to RDPPay.